Information Security
IT Risk Management and information security
Addressing IT risks is part of Group Risk Management
VIG has established a mandatory IT Risk Management approach for the Group through the dedicated IT Risk Management Group Guideline. The guideline is a holistic take on specifically addressing IT and therefore the identification, analysis and evaluation of the risks involved using information technology in all its facets. Furthermore, group requirements for setting IT controls, running business impact analyses and IT continuity management targets are formulated within this document.
There is a quarterly Risk Committee held to inform the management on a regular basis (including IT Risk Management aspects). Furthermore, ad hoc developments can and are directly communicated to the management board member responsible for IT.
Three fundamental protection goals: confidentiality, integrity and availability
At VIG, the IT security aims at protecting electronic information and data, information systems, applications, hardware and infrastructure against threats in order to assure the continuity of the business, to minimize business risk, to safeguard know-how, to comply with legal requirements and to maintain business opportunities. Thus, the security of this electronic information and information systems constitutes a necessity for the achievement of essential company objectives and the continuing success of the Group.
To achieve the best protection of information assets and data of our customers VIG focuses on three fundamental protection goals:
- Confidentiality
information is accessible only to authorized users - Integrity
accuracy and completeness of information and processing methods - Availability
authorized users have access to information and associated assets according to requirements
VIG takes comprehensive security measures for the IT landscape to prevent cybercrime and guarantee that protection goals are met. All globally active external IT service providers have extensive certifications in accordance with international standards for information security like ISO 27001 or can provide reports according to ISAE 3402, which are also renewed regularly. To ensure an effective implementation of an Information Security Management System (ISMS) all internal VIG IT entities are ISO 27001 certified.
Multi-layered security
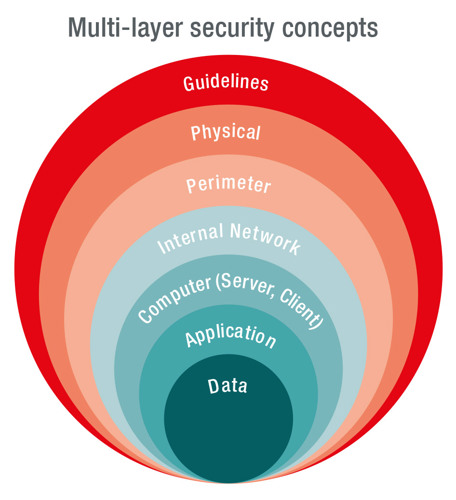
In general, multi-layer security concepts (Defense in Depth) are used to protect data against a wide range of attack vectors and to reduce the probability of an attack being successful.
The outermost layer consists of the IT Security Group Guideline, which is binding for all companies of the Group and whose implementation is monitored by conducting compliance audits. The VIG IT Security Guideline is regularly reviewed and updated. Apart from the guideline VIG companies define additional local IT security measures that consider specific local requirements and legal provisions.
In addition to the basic protection of data centers and server rooms (physical security) by means of access control, alarm systems and monitoring systems, routers and firewalls are used in the outer network area (perimeter security), with very restrictively configured access rights to the layers below. Secured VPNs (Virtual Private Networks) allow controlled and protected access to internal IT systems by authorized persons outside the VIG network. Intrusion detection and intrusion prevention systems are also used to detect and prevent attacks at an early stage. In the internal area of the network, mutually secured network segments are formed for structuring, effective administration and control of access authorizations in order to have separate network segments in case of any cyber-attack attempt.
All servers, IT-devices and applications are protected by appropriate configuration of security-related parameters e.g.:
- Authorization for data and system access follows “need to know principle”
- Use of complex passwords
- Automatically activated screen lock after a defined time of user inactivity
- Filter systems for certain web pages and applications
- Virus scanners
- Regular software updates
- Regular data back-ups
- Data encryption






